EclipseAditya
Loading... 0%

What I think about security?
Security is a journey, not a destination. Every vulnerability discovered, every threat mitigated, and every system hardened brings us one step closer to a more secure digital world.
Skills Matrix
Technical Arsenal & Expertise Areas
Python
Developing custom security tools, AI-driven backends, and network analysis scripts
C/C++
Low-level programming for malware development, evasion techniques, and shellcoding
JavaScript / TypeScript
Full-stack applications, interactive UIs (React, Next.js), and Node.js backends
Solidity
Designing and implementing smart contracts on the Ethereum blockchain for dApps
SQL
Database design, complex queries, and understanding internals for administration and exploitation
Bash
Complex CLI tools and automation scripts with TUI (Whiptail) and system integration
Assembly (x86/x64)
Static malware analysis and crafting custom shellcode
Continuous Learning & Adaptation
The skills section highlights areas I have worked on and gained knowledge in, ranging from beginner to advanced levels. I can also quickly adapt and advance in these skills further if required.
Projects & Case Studies
Real-world cybersecurity implementations and research
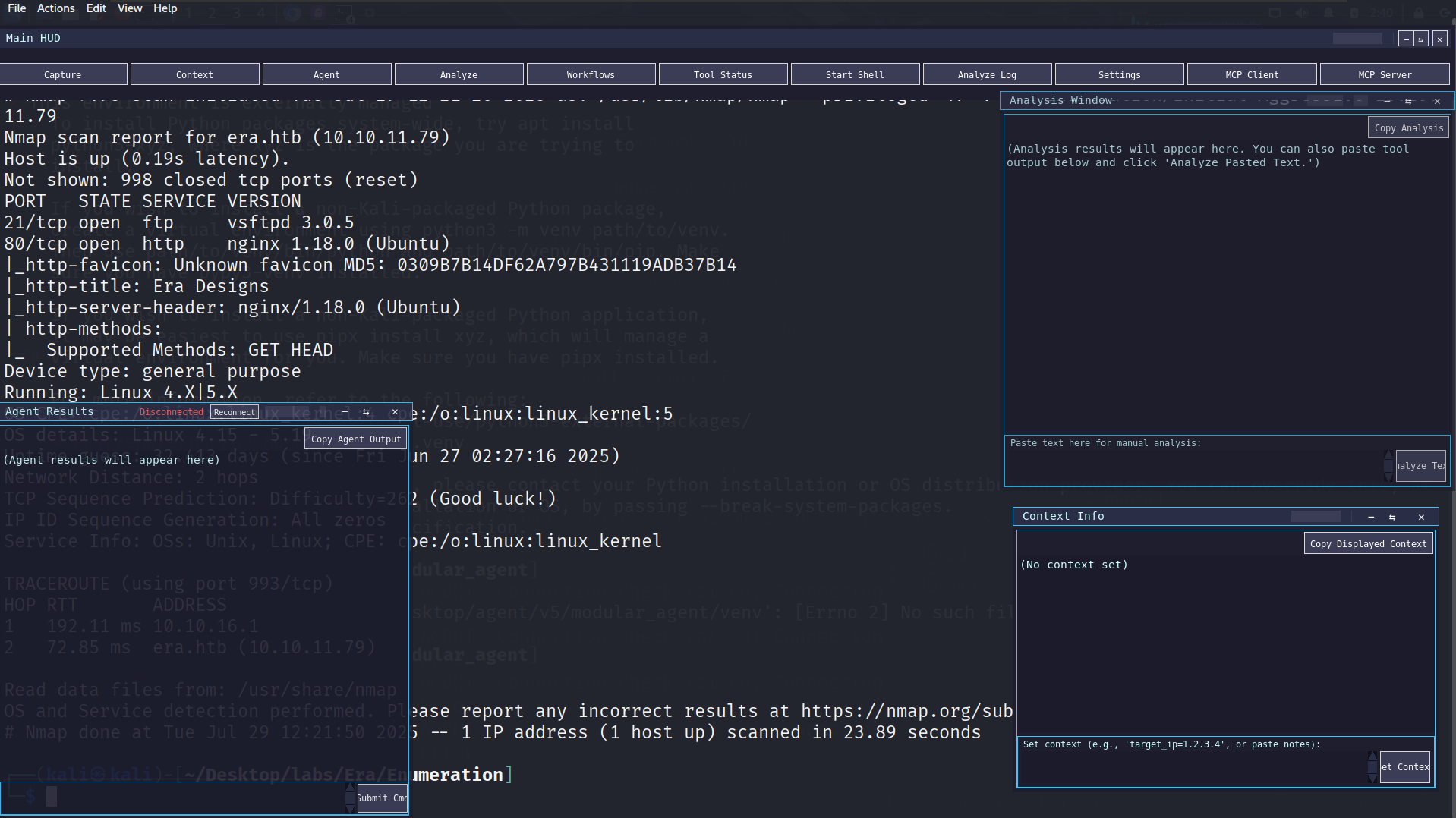
Penetration Testing
Comprehensive AI-enhanced pentesting assistant featuring a Python/Tkinter desktop agent for Kali Linux and Flask backend system with LLM integration, RAG capabilities, and custom MCP protocol for tool orchestration.
Blockchain Security
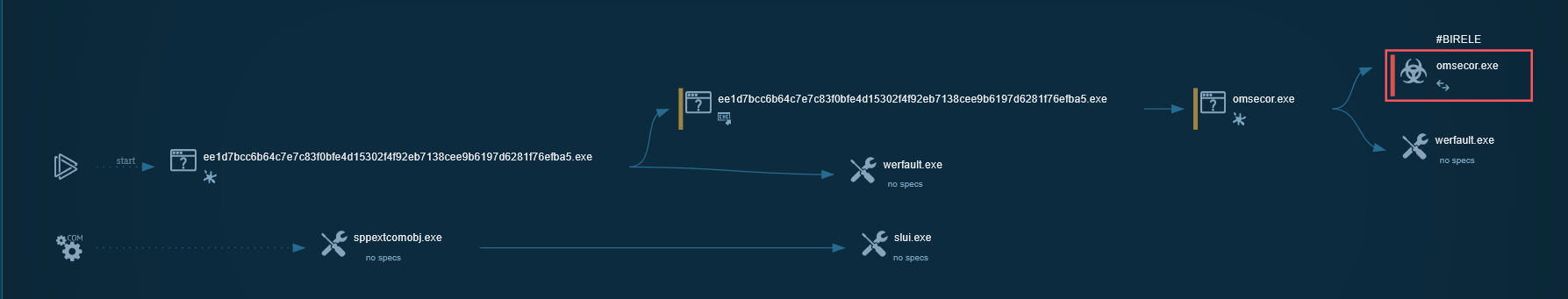
Malware Analysis
Comprehensive static and dynamic analysis of Birele Ransomware samples including MPRESS-packed executables and Emotet/Heodo delivery mechanisms, with detailed behavioral mapping to MITRE ATT&CK framework.
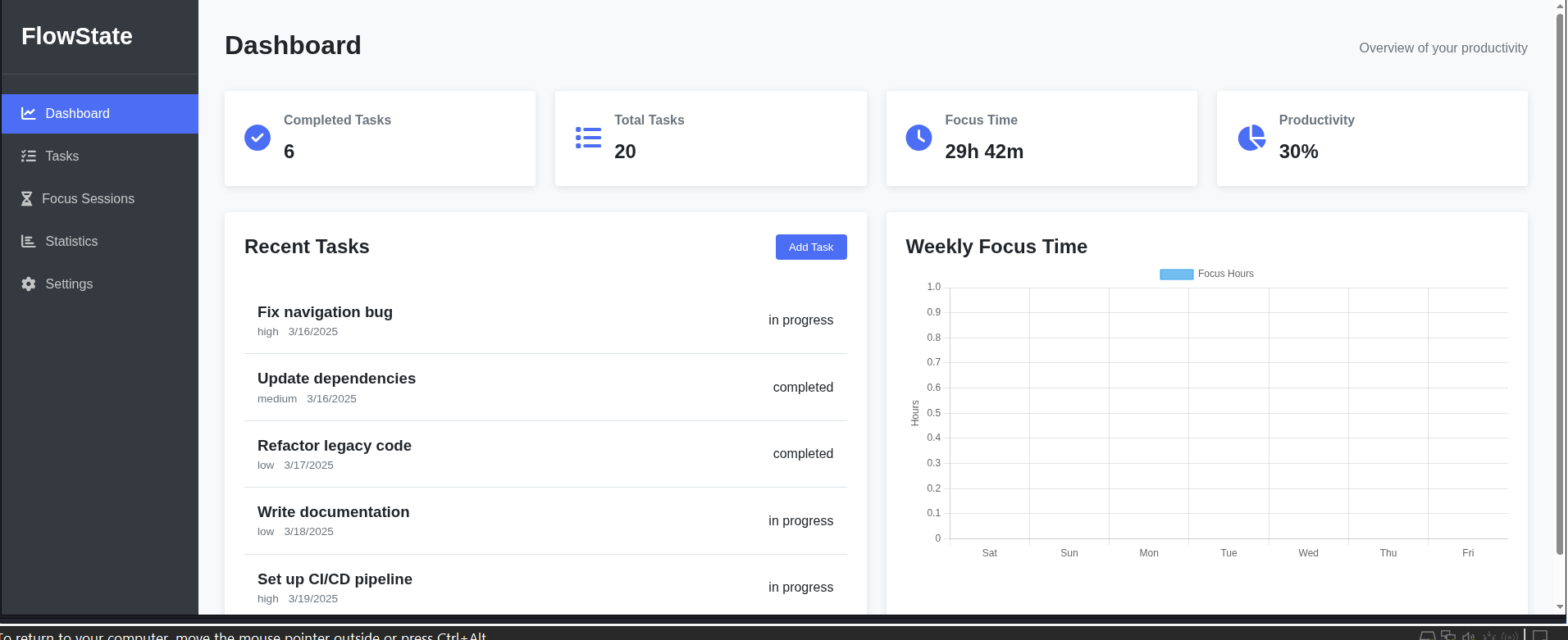
Full-Stack Development
Comprehensive productivity platform featuring a FastAPI web application with task management, Pomodoro timers, data visualization, and an advanced Bash CLI scheduler with system integrations including cron automation, website blocking, and analytical reporting.
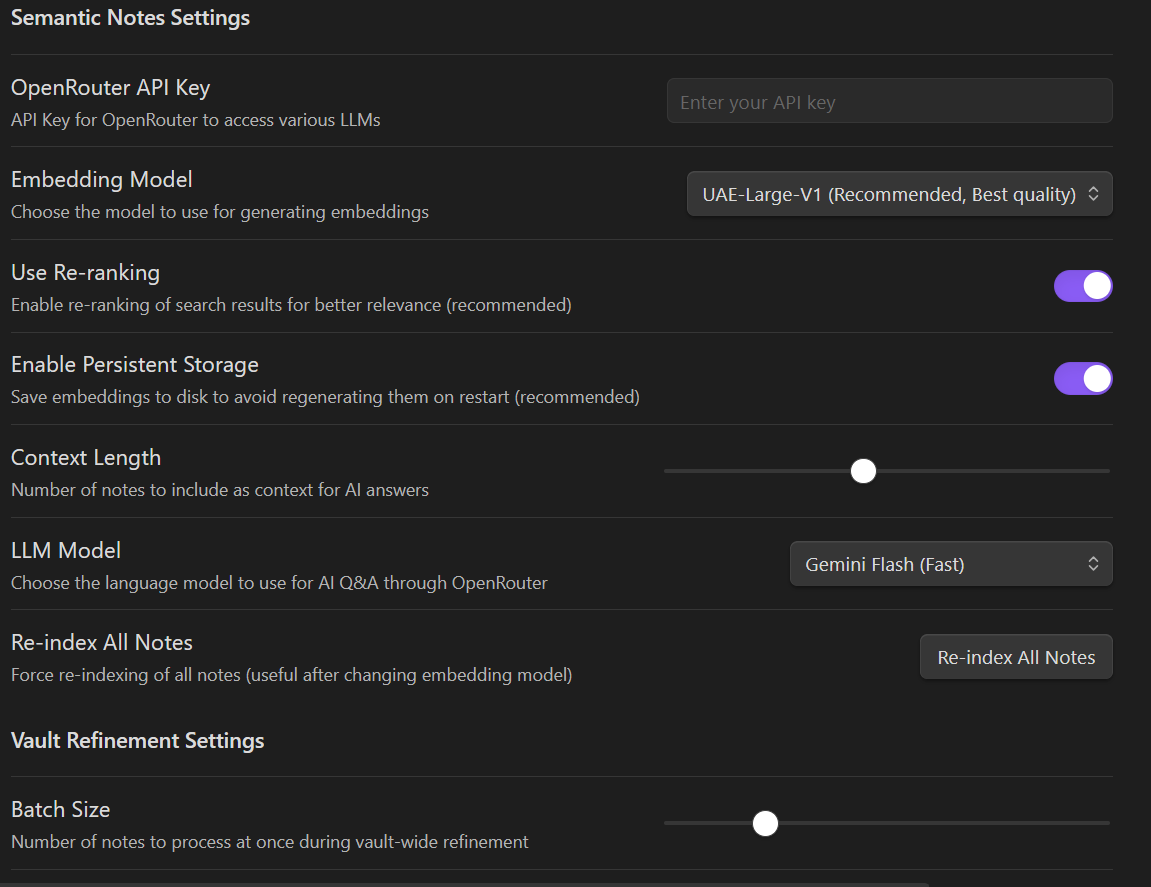
AI/NLP
Advanced Obsidian plugin integrating AI-powered semantic search and RAG-based Q&A capabilities for intelligent personal knowledge management and note interaction with configurable embedding models and LLM integration.
AI/NLP
Advanced AI-powered email security system combining machine learning with psychological intent analysis to detect phishing attempts, featuring ensemble models, TF-IDF vectorization, and real-time threat assessment with 96.77% accuracy.
Want to explore all my projects and contributions?
View All Projects on GitHubProfessional Experience
Career journey in cybersecurity and information security

Head of Research
IEEE Women in Engineering
Led research initiatives and coordinated technical projects at Bennett University's IEEE WIE chapter.
Key Responsibilities
- •Led research initiatives in emerging cybersecurity technologies
- •Coordinated technical workshops and training sessions
- •Mentored junior members in research methodologies
- •Collaborated with faculty on cybersecurity research projects
Technologies & Tools
Key Achievements
- ★Successfully led multiple research initiatives
- ★Improved chapter's research output and quality
- ★Developed comprehensive research framework for cybersecurity projects

Core Member
Async - Official Freelance Club @Bennett University
Active core member contributing to freelance community building and skill development programs.
Key Responsibilities
- •Organized workshops on cybersecurity and ethical hacking
- •Mentored students in freelancing and technical skills
- •Contributed to club's technical content and resources
- •Participated in organizing hackathons and coding competitions
Technologies & Tools
Key Achievements
- ★Successfully organized multiple technical workshops
- ★Helped establish strong cybersecurity focus within the club
- ★Mentored 20+ students in technical skills
Ready for New Challenges
I'm always interested in discussing new opportunities in cybersecurity, whether it's penetration testing, threat intelligence, or security research. whether it's penetration testing, threat intelligence, or security research.
Educational Journey
Academic foundation building expertise in cybersecurity and computer science
Research Leadership
Head of Research
Led research initiatives at IEEE WIE chapter
Academic Performance
8.5/10.0 CGPA
Consistent academic excellence in CSE
Community Engagement
Core Member
Active leadership in student organizations
Specialization Focus
Cybersecurity
Specialized track in information security

Bachelor of Technology in Computer Science
Cybersecurity & Information Systems
Comprehensive computer science program with specialized focus on cybersecurity, ethical hacking, and information systems security.
Relevant Coursework
1st & 2nd
3rd & 4th
5th & 6th (Current)
Key Achievements
- ★Head of Research - IEEE Women in Engineering (Aug-Nov 2024)
- ★Core Member - Async Freelance Club (Oct 2023-May 2024)
- ★Active participant in cybersecurity competitions and CTFs
- ★Maintained consistent academic performance while pursuing certifications
Academic Projects
- •Blockchain Medical Records System (Full-Stack DApp)
- •AI-Powered Pentesting Assistant
- •Network Security Toolkit in Python
- •FlowState Productivity Management System
Extracurricular
- •IEEE Women in Engineering - Research Leadership
- •Async Freelance Club - Technical Workshops
- •Cybersecurity Study Groups & Peer Learning
- •Open Source Contributions & GitHub Projects

Higher Secondary Education
Science (PCM + Computer Science)
Strong foundation in mathematics, physics, and computer science with early exposure to programming and logical thinking.
Relevant Coursework
Class XI & XII
Key Achievements
- ★Consistent academic performance throughout school years
- ★Early interest in computer science and programming
- ★Developed foundational understanding of mathematics and physics
- ★Participated in school science exhibitions and computer competitions
Academic Projects
- •Basic C++ Programming Projects
- •Computer Science Board Project
- •Mathematics & Physics Problem Solving
- •Early Web Development Experiments
Extracurricular
- •Computer Science Club Participation
- •Inter-school Programming Competitions
- •Science Exhibition Projects
- •Mathematics Olympiad Preparation
Continuous Learning Journey
Committed to staying at the forefront of cybersecurity education through formal academics, industry certifications, and hands-on practical experience.
Certifications
Professional credentials and industry certifications
Active Certifications

Google CyberSec
Google Cybersecurity Certificate
Google (Coursera)
8-course program covering cybersecurity fundamentals, risk management, network security, Linux, SQL, SIEM tools, and Python automation
Key Skills

THM Jr. PenTest
TryHackMe Jr. Penetration Tester
TryHackMe
Comprehensive penetration testing path covering web hacking, network security, and privilege escalation
Key Skills

OS Specialization
Introduction to Operating Systems
University (Coursera)
4-course specialization covering virtualization, memory management, concurrency, and persistence in operating systems
Key Skills

DP & Greedy
Dynamic Programming & Greedy Algorithms
CU Boulder (Coursera)
Advanced algorithm design course covering divide and conquer, dynamic programming, greedy algorithms, and NP-completeness
Key Skills
HTB Academy
Hack The Box Academy & Labs
Hack The Box
Hands-on cybersecurity training platform with practical penetration testing labs, modules, and real-world attack scenarios
Key Skills
Planned Certifications
HTB CPTS
Hack The Box Certified Penetration Testing Specialist
Hack The Box
Advanced hands-on penetration testing certification (Currently in progress - more than halfway through)
PortSwigger Labs
PortSwigger Web Security Academy Labs
PortSwigger
Hands-on web security labs covering SQL injection, XSS, XXE, SSRF, and advanced web vulnerabilities (Ongoing practice)
OSCP
Offensive Security Certified Professional
Offensive Security
Industry-standard penetration testing certification
Contact Me
For sensitive communications, use GPG encryption to protect your messages
Step 0: Download Public Key
Download aditya_pubkey.ascStep 1: Import Public Key
Import my public key to your GPG keyring
gpg --import aditya_pubkey.ascStep 2: Encrypt Your Message
Encrypt your message file using my public key
gpg --encrypt --recipient "aditya75pandey@gmail.com" your_secret_msg.txtStep 3: Send Encrypted File
Send the encrypted .gpg file through any of my contact channels
# Send the your_secret_msg.txt.gpg file through any contact methodSecurity First
For highly sensitive communications, always use GPG encryption. Regular emails and messages are suitable for general inquiries and collaboration discussions.
GPG Key Fingerprint:
Available in downloaded public key file